Attack Surface Management Today
The Evolution of Attack Surface Management Tooling
The concept of attack surface management (ASM) has evolved from a mere inventory of known assets to a sophisticated discipline that focuses on understanding and securing an organization’s digital footprint. This evolution is driven by the proliferation of domain-specific security tools purchased to monitor and secure the different enterprise network environments. In a complex landscape, even the basics of maintaining an accurate understanding of asset inventory becomes a daunting task. This complexity underscores the emergence of Cyber Asset Attack Surface Management (CAASM) as a key function for security engineering and operations teams. However, a fundamental challenge remains: most tools in the CAASM space focus on solving the problem of inventorying assets and identifying those that are missing security agents, but lack a contextual mapping of the enterprise attack surface. True attack surface mapping involves correlating the enterprise security stack and connecting the dots between each asset to understand what is truly at risk.
Why Attack Surface Management is Critical for Security
Attack Surface Management is at the very core of security’s role in the enterprise. The primary function is to oversee the identification and management of the enterprise’s cyber assets, reducing the likelihood of security breaches, and ensuring the continuity of operations. A complete mapping of an enterprise attack surface includes the complete discovery of all assets requiring protection, their vulnerabilities, security metadata, their connectivity across the enterprise network, and their exposure to the outside. Without complete comprehension of the attack surface, breach likelihood increases because risk mitigation is misaligned with actual risk, incident response takes longer without an understanding of the blast radius, and business operations are more likely to be slowed or brought down altogether.
Overcoming Complexity to Map the Attack Surface
The security stack: everything, everywhere, all at once
You have a lot of tools and tons of data, and they are distributed across teams and network environments. Network infrastructures have undergone significant evolution, transitioning from traditional on-premises physical setups to virtualized environments, and further expanding into public cloud and IoT domains. This progression has given rise to a range of specialized tools, each tailored for specific segments of the network yet often operating in silos, unable to communicate effectively with one another. Each brings its different data points and types, creating a massive challenge in aggregating and making sense of this information. This is particularly challenging in cloud environments where assets are not static and change often. The result is often an overwhelming amount of data that surpasses the capacity of security teams to manage and prioritize risk effectively. That’s why data convergence needs to be integrated, optimized, and accessible to ensure the accuracy and accessibility of trustworthy data to those who need it to enable the business.
Innovative High-Fidelity Data Convergence for Attack Surface Mapping
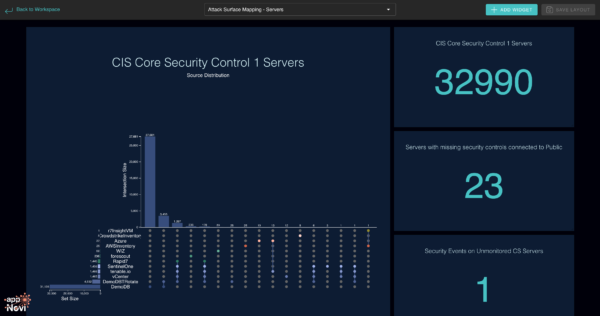
An example of appNovi’s reporting on the attack surface of servers
To address these challenges, appNovi has developed a flexible data and integration model that begins by integrating with all sources of data that maintain and monitor assets. Crucially, assets encompass more than just laptops and servers; they include users, applications, code, and various other components that form an organization’s digital landscape. Cyber asset inventories are created through automated deduplication and enrichment processes to understand what every tool says about an asset. We utilize connection data from NDR and SIEM platforms, going beyond creating an inventory to mapping the interconnectivity of all elements. This includes not only network links but also user access relationships. Additionally, we enrich this data with telemetry to gain insights into both the network’s framework and its business context. The combination of all these data points allows appNovi to provide a comprehensive understanding of the attack surface, mapping it from the inside out.
Maintaining Inventories in Dynamic Environments
Modern networks are typically composed of various environments, including hybrid clouds, software-defined networks (SDN), and bare metal servers. With different teams responsible for different network environments, new hires onboarded, new code pushed, and new infrastructure commissioned or decommissioned, there is constant cyber asset change across all network environments. This is why any attack surface management solution must go beyond just building inventories at a single moment to include tracking how assets and connections between them change.