Attack Surface Management: The Most Effective Method of Risk Prioritization
This is part of an Attack Surface Mapping blog series. To understand the current challenges with Attack Surface Mapping, visit our prior article.
Beyond Asset Visibility: Gaining Deep Insights
IT and security teams understand it’s not just about seeing what cyber assets are present. They must have deep insights into every asset, including its interconnectivity within the network, its owner, its risk profile, and the dependencies of the asset. This level of understanding requires a system that can make sense of the technical complexities in a normalized, easily searchable data format. Users can explore this data based on specific queries or through broader exploration, allowing for a detailed understanding of their network’s security posture.
Identifying Exposure: A Multi-Dimensional Approach
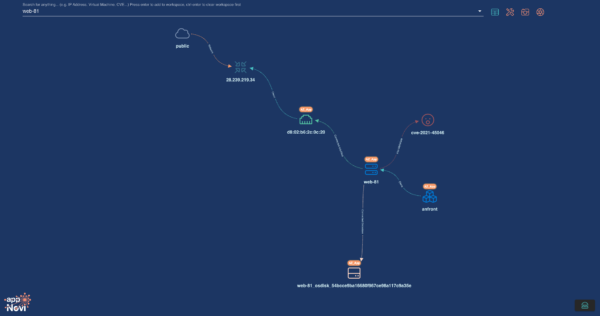
Assessing Publicly Known Exploits: Many tools report on vulnerability data. All data must be converged to understand the complete picture. The convergence and enrichment of data provides a comprehensive understanding including exploitability and risk across all vendor scores. When all of your tools’ intelligence is aggregated, you better understand what is exploitable, what is generally being exploited, and the prevalence of these riskier assets in your environment to better prioritize enterprise patching. Understanding Network Exposure: The next level of enrichment for prioritizing the risk of vulnerabilities is correlating their exposure based on necessary access for exploitation. For instance, among assets with remote-based vulnerabilities, appNovi can determine which ones connect to the internet with the specific port and protocol needed for exploitation. Or the locally vulnerable assets owned by users most frequently targeted by phishing attacks. Or those assets belonging to users with a higher historical propensity to fall victim to phishing. When network context is understood, security teams also identify assets that, while not directly exposed, are probable pivot points in an attack chain due to their network connections.
The Importance of Business Context in Attack Surface Mapping for Vulnerability Prioritization
One of the most critical aspects of attack surface mapping is understanding the business impact of each asset. This means identifying which assets are part of critical applications and further categorizing them based on their importance to the business. By combining the context of network and business data with risk assessments, appNovi doesn’t just map the attack surface but also achieves effective risk prioritization driven through contextual exposure and business impact. Often organizations do not know the applications deployed in their network – exploring cyber asset data to understand network connections between known application assets and other assets to map out dependencies is a key reconnaissance endeavor to eliminate the ambiguity of applications. The result of incorporating the direct and indirect impact of risk to application dependencies enables bespoke risk prioritization for the enterprise. 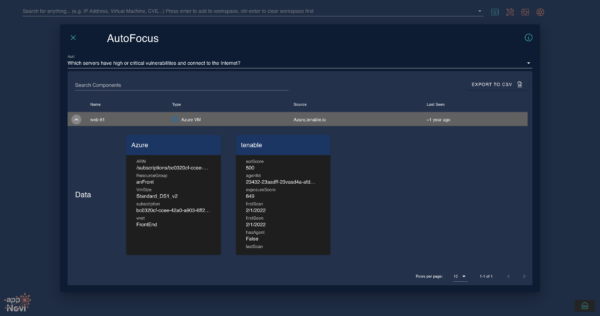
This is part of an ongoing blog series covering Attack Surface Mapping for enterprises. Continue reading about Attack Surface Mapping’s impact on vulnerability prioritization in the next blog.