by Dan Rheault | Mar 22, 2023 | Blog, Incident Response, Thought Leadership
Cybersecurity Mesh Architecture simply empowers your incident response handlers to make decisions based on a complete understanding of the environment. This efficiency is gained inexpensively by eliminating data wrangling and reliance on Excel through integration with...

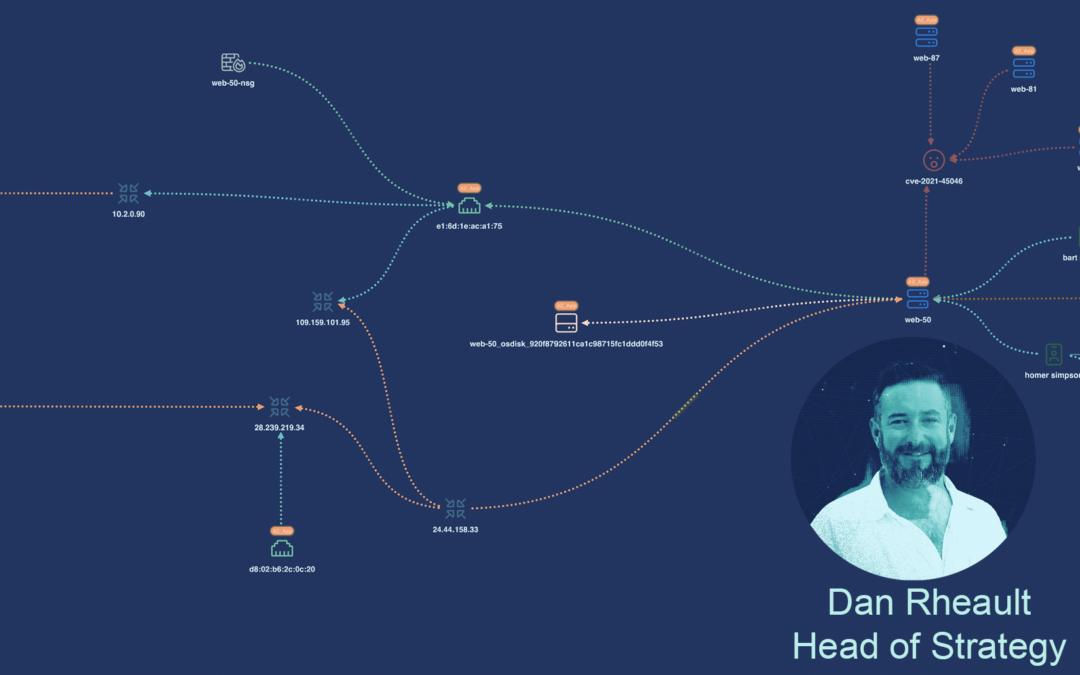
by Dan Rheault | Mar 2, 2023 | Blog, Thought Leadership, Vulnerability Management
Every enterprise must identify and manage vulnerabilities across the network. And the network continues to change – bare metal machines, virtual infrastructure, and the increasing prevalence of containers. But IT assets are more than just infrastructure – they include...

by Dan Rheault | Feb 9, 2023 | Blog, Thought Leadership
“Oh good, more alerts” Tools monitor, alert, and refine. Analysts aggregate, analyze, and file a ticket. The cycle continues. Burnout continues. Turnover in the SOC continues. Upleveling analysts takes time. The SOC spends more time using the tools they have...

by Dan Rheault | Feb 1, 2023 | Thought Leadership
About This is the text of a formatted whitepaper available here. Security operations teams must develop an effective vulnerability management strategy. A new solution for ensuring effectiveness is through meshing existing data to achieve context. Ensuring...

by Dan Rheault | Jan 18, 2023 | Blog, Thought Leadership
What is network dependency mapping? Network dependency mapping is the process of identifying dependencies between different network assets. Historically this has been a complex task due to reliance on manual analysis of disparate data sets including CMDBs,...

by Dan Rheault | Jan 10, 2023 | Blog, Thought Leadership
IT asset management is the ongoing identification, classification, and risk management of IT assets across the enterprise network. IT assets can be workstations, servers, mobile devices, IoT, and other network-connected devices. One of the oldest adages in security is...






