
by Dan Rheault | Jul 20, 2023 | Blog, Thought Leadership
Today’s cybersecurity landscape is increasingly complex with a constantly changing attack surface. The rate of change often obscures cyber assets in their entirety, which presents a growing challenge for organizations seeking to safeguard their critical cyber assets....

by Dan Rheault | Apr 20, 2023 | Blog, Thought Leadership
In the digital age every enterprise heavily relies on technology to manage and grow its business. As technology becomes more complex and siloed, it has become increasingly difficult for enterprises to keep track of all their IT assets. IT asset discovery and...
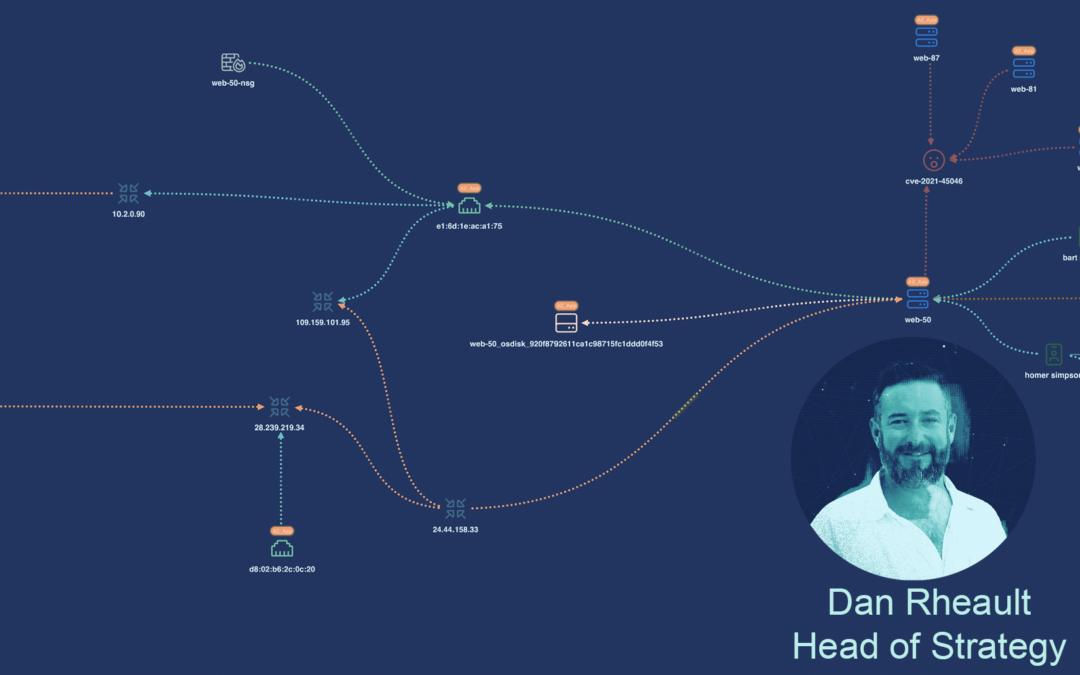
by Dan Rheault | Mar 22, 2023 | Blog, Incident Response, Thought Leadership
Cybersecurity Mesh Architecture simply empowers your incident response handlers to make decisions based on a complete understanding of the environment. This efficiency is gained inexpensively by eliminating data wrangling and reliance on Excel through integration with...

by Dan Rheault | Mar 2, 2023 | Blog, Thought Leadership, Vulnerability Management
Every enterprise must identify and manage vulnerabilities across the network. And the network continues to change – bare metal machines, virtual infrastructure, and the increasing prevalence of containers. But IT assets are more than just infrastructure – they include...

by Dan Rheault | Feb 9, 2023 | Blog, Thought Leadership
“Oh good, more alerts” Tools monitor, alert, and refine. Analysts aggregate, analyze, and file a ticket. The cycle continues. Burnout continues. Turnover in the SOC continues. Upleveling analysts takes time. The SOC spends more time using the tools they have...

by Dan Rheault | Jan 18, 2023 | Blog, Thought Leadership
What is network dependency mapping? Network dependency mapping is the process of identifying dependencies between different network assets. Historically this has been a complex task due to reliance on manual analysis of disparate data sets including CMDBs,...






