Automox integration
Ensure complete agent coverage for complete visibility, vulnerability prioritization, and automated remediation

Supported Products
- Automox
appNovi integrates with Automox and your other data sources to identify all cyber assets across the enterprise network. appNovi converges Automox data with other infrastructure data sources to automatically maintain an enriched and authoritative source of all cyber assets. appNovi integrates with Automox to support Cyber Asset Attack Surface Mapping (CAASM) and remediation.
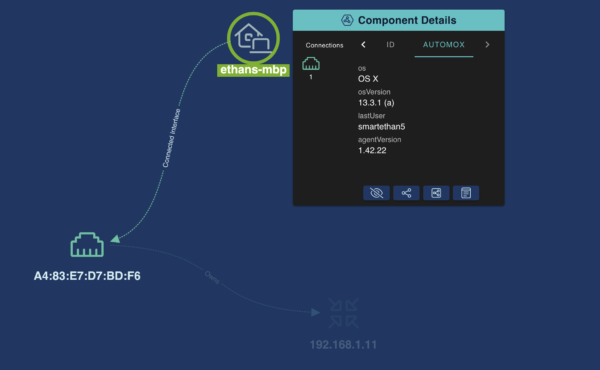
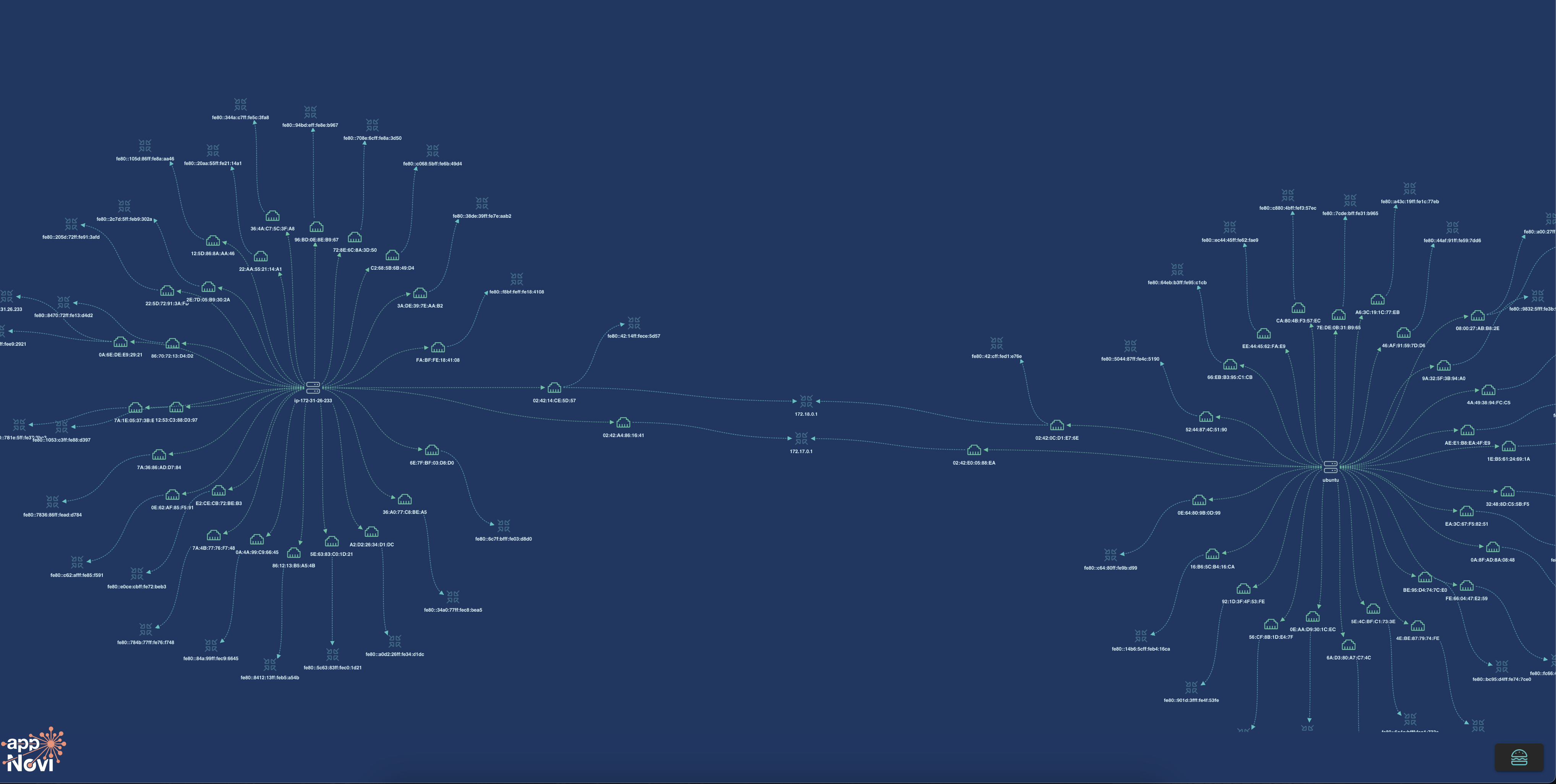
appNovi meshes Automox data with your other data sources to identify all cyber assets, security controls, and their context enrichment. appNovi identifies assets missing Automox agents and through integrated actions enables remediation using existing workflows and playbooks. And with telemetry enrichment, you can prioritize those cyber assets which are internet-facing or business application-impacting through Cyber Asset Attack Surface Mapping (CAASM).
Related Integrations

Tanium
ExtraHop
Rapid7
Panther
Fortinet
Crowdstrike
Case Studies
Developing a business-specific risk reduction plan with security data visualization
Leveraging cybersecurity mesh to implement business-specific vulnerability management
Solution Briefs
appNovi Solution Brief
Learn about the appNovi cybersecurity mesh platform for attack surface identification and mapping, vulnerability management, and incident response enablement.
Resources
Explore how appNovi can help you align to CIS controls to mature vulnerability management, attack surface mapping, incident response, and data center migration processes.