Qualys integration
Leverage business-specific vulnerability management through cybersecurity mesh architecture
The Qualys Cloud Platform and its integrated apps help businesses simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum of auditing, compliance and protection for IT systems and web applications. You can learn more about Qualys at www.qualys.com.

Supported Products
- QualysGuard
- QualysVMDR
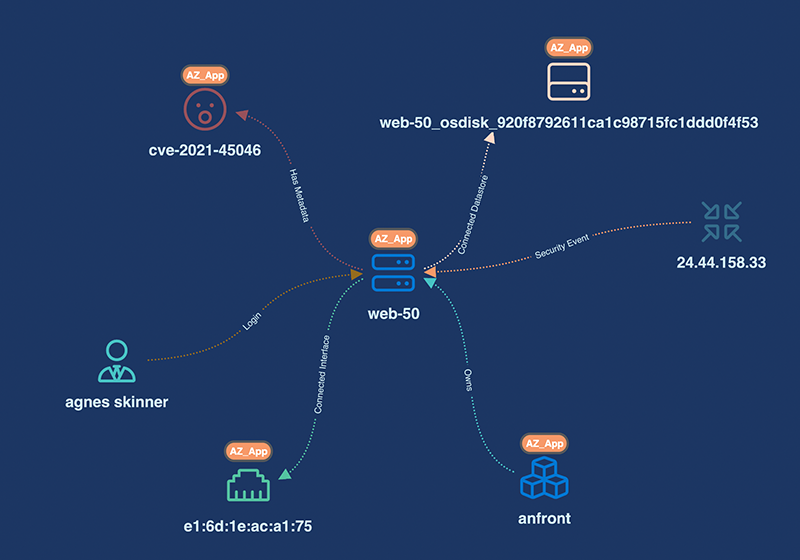
appNovi integrates with Qualys products to retrieve IT assets identified through scan events and installed agents. appNovi integrates Qualys data with other IT asset data sources to provide a searchable aggregate repository of your enterprise’s infrastructure to support cyber asset attack surface management and incrementally adopt a cybersecurity mesh architecture.
When contextually converged with other data sources such as NetFlow, vulnerability, or identity data appNovi visualizes your network asset connections to understand the business impact of risk.

appNovi integrates with Qualys solutions to retrieve IT asset, vulnerability, and agent status data to help you identify control gaps in asset management and agent coverage. Qualys vulnerability aggregates with other data sources such as network traffic to analyze vulnerable IT assets’ contextual exposure for exploitation to enhance vulnerability management, risk prioritization, attack surface identification and discovery, and incident response.
Related Integrations
Tenable
Cisco
Rapid7
Crowdstrike
Fortinet

SentinelOne
Case Studies
Developing a business-specific risk reduction plan with security data visualization
Leveraging cybersecurity mesh to implement business-specific vulnerability management
Solution Briefs
appNovi Solution Brief
Learn about the appNovi cybersecurity mesh platform for attack surface identification and mapping, vulnerability management, and incident response enablement.
Resources
Explore how appNovi can help you align to CIS controls to mature vulnerability management, attack surface mapping, incident response, and data center migration processes.